THM Writeup – Anthem

Exploit a Windows machine in this beginner level challenge
This task involves you, paying attention to details and finding the ‘keys to the castle’.
This room is designed for beginners, however, everyone is welcomed to try it out!
Enjoy the Anthem.
In this room, you don’t need to brute force any login page. Just your preferred browser and Remote Desktop.
Add IP address to your hosts file:
echo '10.10.232.68 anthem.thm' >> /etc/hostsScan the target machine – find open ports first:
nmap -n -Pn -sS -p- --open -min-rate 5000 -vvv anthem.thm
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 128
3389/tcp open ms-wbt-server syn-ack ttl 128
5985/tcp open wsman syn-ack ttl 128Get more details about open ports:
nmap -T4 -A -p 80,3389,5985 anthem.thm
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=WIN-LU09299160F
| Not valid before: 2022-02-14T07:03:10
|_Not valid after: 2022-08-16T07:03:10
|_ssl-date: 2022-02-15T07:05:18+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not FoundNow you can answer two questions:
What port is for the web server?
What port is for remote desktop service?
Directory bruteforce web application:
gobuster dir -u http://anthem.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
/search (Status: 200)
/blog (Status: 200)
/sitemap (Status: 200)
/rss (Status: 200)
/archive (Status: 301)
/categories (Status: 200)
/authors (Status: 200)
/Search (Status: 200)
/tags (Status: 200)
/install (Status: 302)
/RSS (Status: 200)
/Blog (Status: 200)
/Archive (Status: 301)
/SiteMap (Status: 200)
===============================================================Note: So you know – I did not let the scan finish, stopped it earlier.
In the meantime find an answer for another questions:
What is a possible password in one of the pages web crawlers check for?
Browse to http://anthem.thm/robots.txt
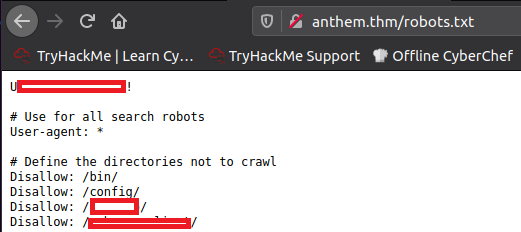
What CMS is the website using?
As we saw in robots.txt and also when we browse to http://anthem.thm/install
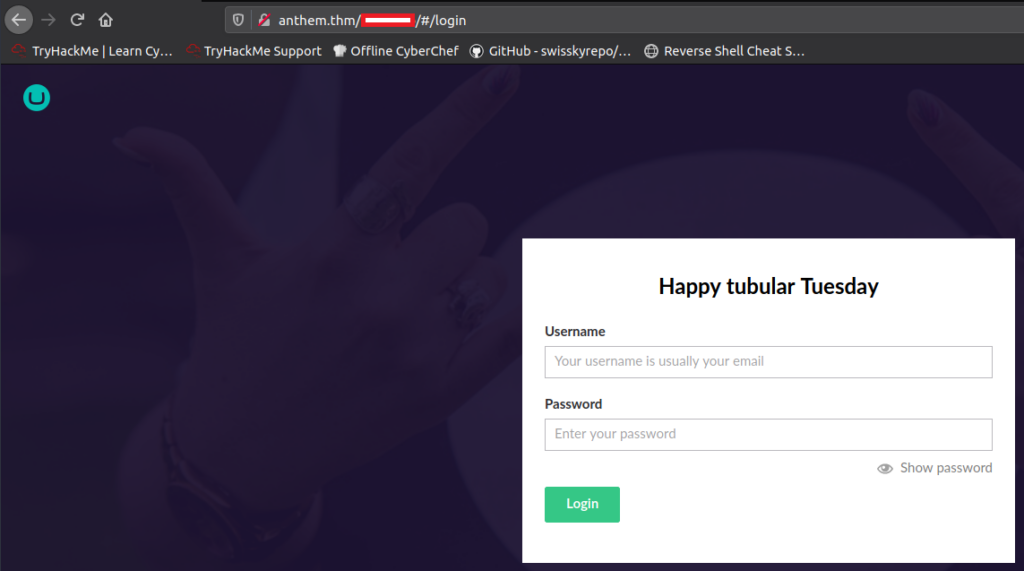
What is the domain of the website?
Browse back to http://anthem.thm/ and scroll down:
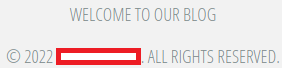
What’s the name of the Administrator
Browse to http://anthem.thm/archive/a-cheers-to-our-it-department/
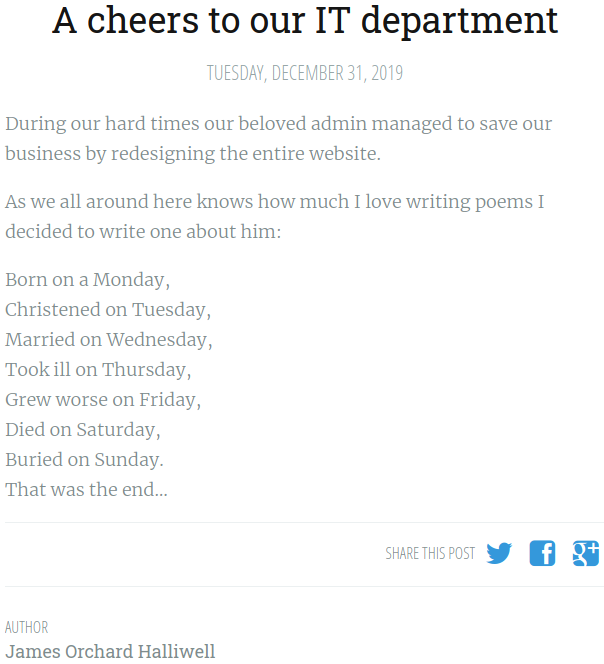
There is an article about admin and a poem, now seach for the poem:
Can we find find the email address of the administrator?
Browse to http://anthem.thm/archive/we-are-hiring/
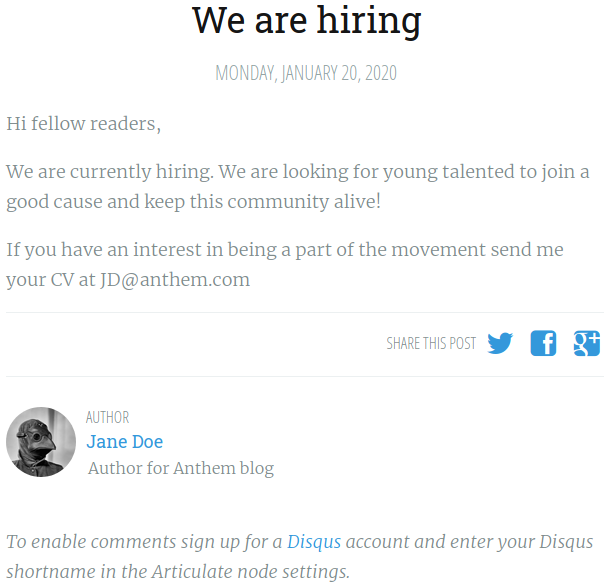
There is an article that contains employee’s email address – if we use this pattern and the name we found (previous question), we should have admin’s email address.
What is flag 1?
Browse to http://anthem.thm/archive/we-are-hiring/ and view the page source:
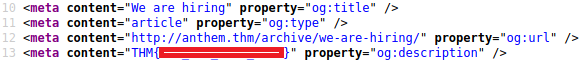
What is flag 2?
Browse to http://anthem.thm/ and view the page source:
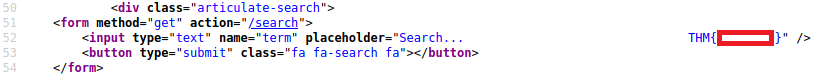
What is flag 3?
Browse to http://anthem.thm/authors
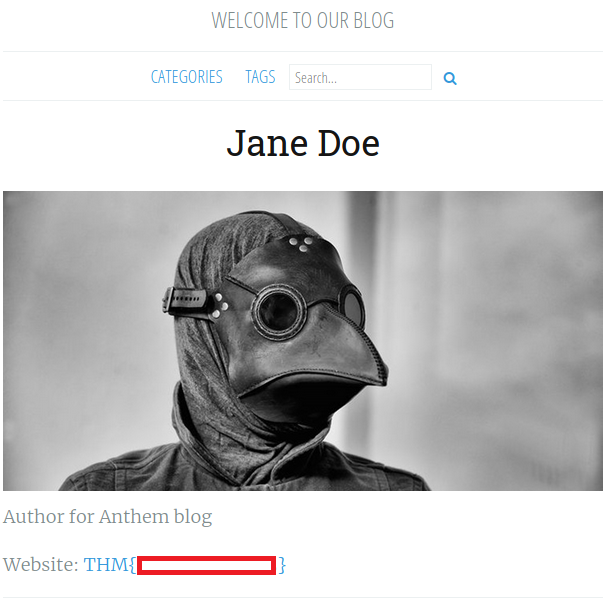
What is flag 4?
Browse to http://anthem.thm/archive/a-cheers-to-our-it-department/ and view the page source:
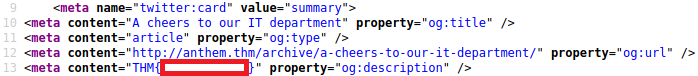
Let’s figure out the username and password to log in to the box.(The box is not on a domain)
Ok, we found a password in robots.txt and the username is, very probably, the first part of the email address.
No answer neededGain initial access to the machine, what is the contents of user.txt?
So let’s try to RDP to the target machine:
xfreerdp /u:[REDACTED] /p:[REDACTED] /v:anthem.thmWe are successfully connected to the target machine:
Now open the user.txt file to read the flag.
Can we spot the admin password?
Open windows explorer, go to C drive and change the view options to show hidden items:
A backup folder appeared.
If we try to open restore.txt that resides in the backup folder, we get permissions denied:
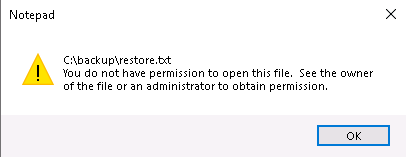
Change restore.txt permissions – right click the file, select Properties > Security > Edit > Add:
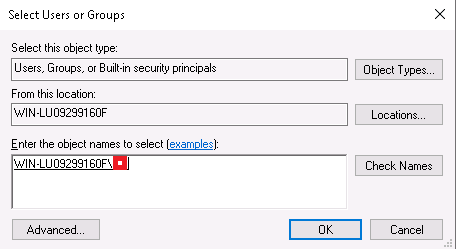
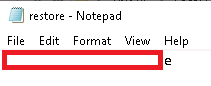
Click OK 3 times and read the file again:
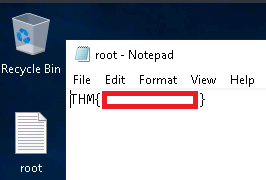
Escalate your privileges to root, what is the contents of root.txt?
Now connect via RDP as administrator:
xfreerdp /u:administrator /p:[REDACTED] /v:anthem.thmRead the root flag on the administrator’s desktop:
Do you like this writeup? Check out other THM Writeups.